I. Background
On November 8, the FBI, the NASA-OIG and Estonian police arrested several cyber criminals in “Operation Ghost Click”. The criminals operated under the company name “Rove Digital”, and distributed DNS changing viruses, variously known as TDSS, Alureon, TidServ and TDL4 viruses. You can read more about the arrest of the Rove Digital principals here, and in the FBI Press Release.
DNSChanger is a malware family that has been around for several years now, and at its height controlled the web browsing of some 4 million PCs. DNSChanger typically masqueraded as a video codec download, and once downloaded would surreptitiously change the DNS servers of the infected host to rogue DNS servers which direct users to pay-per-click advertising networks to earn money for the perpetrators.
Just recently, the FBI announced that in cooperation with Estonian authorities, they have identified and arrested several people behind the scheme. The rogue DNS servers are now under the control of the authorities, and are configured to act as legitimate DNS servers until a cut-off date of March 8, 2012.
On March 5, 2012. a US District Court (New York) signed a new order to extend the March 8 deadline to July 9, 2012. With the information provided by DCWG, CamCERT has informed the relevant ISPs about this information and we expect the ISPs forwarding our advices to the customers.
II. What is the Impact of DNSChanger infection?
DNSChanger malware primarily spreaded when a user accesses a particular website or downloads online video viewer software and get infected. The DNSChanger malware will secretly alter the DNS settings on the affected computer pointing to the DNS server established by cybercrime ring to completely control DNS to resolve the desired IP address. The cybercrime ring can use DNS Changer botnet to route the users to access specific web sites unknowingly, including replacing the advertisements on web sites that are loaded by users to generate click-fraud or implant other malicious software.
FBI has produced a very nice document that describes the DNS changer malware in detail, in the reference below, along with how to determine your system has been infected, and furthermore provide a table of explicit IPs and IP ranges of rogue DNS servers.
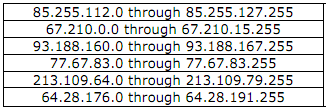
III. How to know that your PC or Braodband Router infected with DNSChanger?
1. The victim’s computer may visit a malicious web site, including phishing website or other malware hosting website. These websites may steal the data in the computer or even control the computer.
2. Start from Jul 9, 2012, since the victim’s computer or broadband router cannot resolve the domain name. Therefore they cannot access the Internet.
To get to know your computer or broadband router is infected with the DNSChanger malware, in accordance with the following steps to check.
Method 1- Use the DCWG EyeChart
Open the web browser (e.g. Internet Explorer, Firefox, Chrome or Safari) to access the testing site provided by DNS Changer Working Group (DCWG): http://dns-ok.us
[gdl_gallery title=”DNSChanger” width=”175″ height=”150″ ]
Method 2- Manually Checking
The following pages would help check to manually see if you have DNS Changer DNS servers configured on your computer. Use of the “check up” pages are more effective, but some would want to check manually.
- Checking for DNS Changer on Windows XP
- Checking for DNS Changer on Windows Vista (pending)
- Checking Windows 7 for Infections
- Checking OSX for Infections
IV. WorldMap of DNSChanger infected by Country
In the graphic above, you can see the CAMBODIA on the list (near China). It means that, some of PCs in our country also infected by DNSChanger malware.
Here is the video illustration about DNSChanger infections from Jan 2012 to March 2012 provided by ShadowServer
[youtube]http://www.youtube.com/watch?v=A3wBR5DT7BU[/youtube]
V. References:
1. https://www.fbi.gov/file-repository/dns-changer-malware.pdf
2. http://www.dcwg.org
3. http://threatpost.com/en_us/blogs/us-judge-extends-life-ghost-click-infected-machines-030612
4. http://www.dcwg.org/fix/
V. Contact Information
– Email: office@camcert.gov.kh
– Tel: (855) 92 335 536 – (855) 16 888 209
[message_box title=”Disclaimer” color=”yellow”]
The information provided herein is on “as is” basis, without warranty of any kind.
[/message_box]









